[ad_1]
A crypto pocketbook manufacturer declared today that cyberpunks might be targeting individuals with an iMessage “zero-day” manipulate– however all indicators indicate an overstated danger, otherwise a downright fraud.
Trust fund Budget’s authorities X (formerly Twitter) account wrote that “we have trustworthy intel pertaining to a risky zero-day manipulate targeting iMessage on the Dark Internet. This can penetrate your apple iphone without clicking any kind of web link. High-value targets are most likely. Each usage elevates discovery threat.”
The pocketbook manufacturer advised apple iphone customers to switch off iMessage totally “till Apple spots this,” although no proof reveals that “this” exists in any way.
The tweet went viral, and has actually been seen over 3.6 million times since our magazine. Due to the focus the article obtained, Trust fund Budget hours later on wrote a follow-up post. The pocketbook manufacturer increased down on its choice to go public, stating that it “proactively connects any kind of possible risks and dangers to the area.”
Trust Budget did not reply to TechCrunch’s ask for remark. Apple agent Scott Radcliffe decreased to comment when gotten to Tuesday.
As it ends up, according to Trust Wallet’s CEO Eowyn Chen, the “intel” is an ad on a dark website called CodeBreach Laboratory, where somebody is providing claimed claimed manipulate for $2 million in bitcoin cryptocurrency. The advert entitled “iMessage Venture” declares the susceptability is a remote code implementation (or RCE) manipulate that calls for no communication from the target– frequently called “zero-click” manipulate– and deals with the current variation of iphone. Some pests are called zero-days since the supplier has no time at all, or absolutely no days, to take care of the susceptability. In this instance, there is no proof of a manipulate to start with.
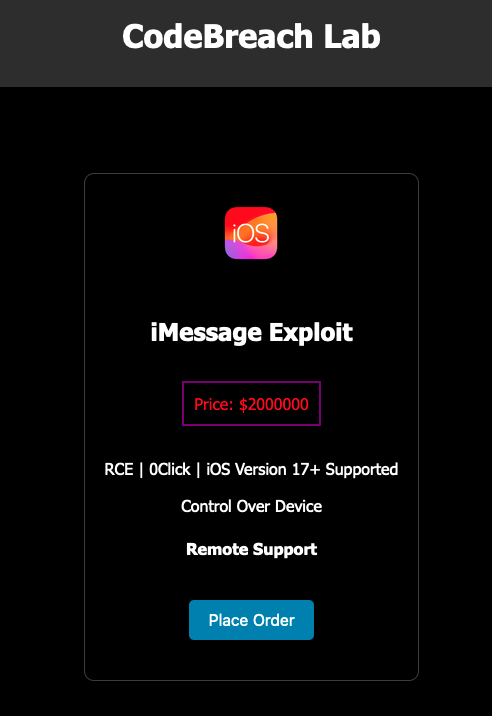
A screenshot of the dark internet advertisement declaring to offer a supposed iMessage manipulate. Photo Credit Scores: TechCrunch
RCEs are a few of one of the most effective ventures since they enable cyberpunks to from another location take control of their target tools online. A make use of like an RCE combined with a zero-click ability is unbelievably useful since those assaults can be performed vaguely without the tool proprietor recognizing. Actually, a business that obtains and re-sells zero-days is currently offering between $3 to $5 million for that sort of zero-click zero-day, which is additionally an indicator of just how tough it is to locate and establish these sorts of ventures.
Get in touch with Us
Do you have any kind of info concerning real zero-days? Or concerning spyware suppliers? From a non-work tool, you can get in touch with Lorenzo Franceschi-Bicchierai safely on Signal at +1 917 257 1382, or using Telegram, Keybase and Cable @lorenzofb, or email. You additionally can get in touch with TechCrunch using SecureDrop.
Offered the scenarios of just how and where this zero-day is being marketed, it’s likely that it is all simply a fraud, which Trust fund Budget succumbed to it, spreading what individuals in the cybersecurity sector would certainly call FUD, or “are afraid unpredictability and uncertainty.”
Zero-days do exist, and have been used by government hacking units for years. However in truth, you possibly do not require to switch off iMessage unless you are a risky customer, such as a reporter or objector under an overbearing federal government, for instance.
It’s far better guidance to recommend individuals switch on Lockdown Mode, an unique setting that disables particular Apple tool attributes and capabilities with the objective of decreasing the opportunities cyberpunks can utilize to strike apples iphone and Macs.
According to Apple, there is no proof anybody has actually efficiently hacked somebody’s Apple tool while utilizing Lockdown Setting. A number of cybersecurity professionals like Runa Sandvik and the researchers that operate at Resident Laboratory, that have actually examined lots of situations of apple iphone hacks, suggest utilizing Lockdown Setting.
For its component, CodeBreach Laboratory seems a brand-new web site without performance history. When we examined, a search on Google returned just 7 outcomes, among which is a blog post on a widely known hacking online forum asking if anybody had actually formerly become aware of CodeBreach Laboratory.
On its homepage– with typos– CodeBreach Laboratory declares to provide a number of sorts of ventures apart from for iMessage, however gives no additional proof.
The proprietors explain CodeBreach Laboratory as “the nexus of virtual disturbance.” However it would possibly be better to call it the nexus of braggadocio and naivety.
TechCrunch might not get to CodeBreach Laboratory for remark since there is no chance to get in touch with the claimed business. When we tried to acquire the affirmed manipulate– since why not– the web site requested for the purchaser’s name, e-mail address, and after that to send out $2 million in bitcoin to a details pocketbook address on the general public blockchain. When we examined, no one has up until now.
Simply put, if somebody desires this claimed zero-day, they need to send out $2 million to a budget that, at this moment, there is no chance to recognize that it comes from, neither– once again– any kind of method to get in touch with.
And there is a great opportunity that it will certainly stay in this way.
[ad_2]
Source link .




